1 Introduction
This document, and the specifications that are derived from it, defines the FIPA Architecture. The parts of the FIPA architecture include:
· A specification that defines architectural elements and their relationships (this document).
· Guidelines for the specification of agent systems in terms of particular software and communications technologies (Guidelines for Instantiation).
· Specifications governing the interoperability and conformance of agents and agent systems (Interoperability Guidelines).
See Section 2, Scope and Methodology for a fuller introduction to this document.
1.1 Contents
This document is organized into the following sections and a series of annexes.
· This Introduction.
· The Scope and methodology section explains the background of this work, its purpose, and the methodology that has been followed. It describes the role of this work in the overall FIPA work program, and discusses the status of the work.
· The Architectural overview presents an overview of the architecture with some examples. It is intended to provide the appropriate context for understanding the following sections.
· The Architecture and Information Model and Architectural Elements comprise the FIPA architecture itself.
· The section Evolution of the Architecture discusses the way in which this document may evolve.
The annexes include:
·
Goals for message transport, directory services, agent
communication language and security.
·
Relationships to existing FIPA specifications.
·
Description of the Abstract ACL.
1.2 Audience
The primary audience for this document is developers of concrete specifications for agent systems – specifications grounded in particularly technologies, representations, and programming models. It may also be read by the users of thee concrete specifications, including implementers of agent platforms, agent systems, and gateways between dissimilar agent systems.
This document describes an abstract architecture for creating intentional multi-agent systems. It assumes that the reader has a good understanding about the basic principles of multi-agent systems. It does not provide the background material to help the reader assess whether multi-agent systems are an appropriate model for their system design, nor does it provide background material on topics such as Agent Communication Languages, BDI systems, or distributed computing platforms.
The abstract architecture described in this document will guide the creation of concrete specifications of different elements of the FIPA agent systems. The developers of the concrete specifications must ensure that their work conform with the abstract architecture in order to provide specifications with appropriate levels of interoperability. Similarly, those specifying applications that will run on FIPA compliant agent systems will need to understand what services and features that they can use in the creation of their applications.
1.3 Acknowledgements
This document was developed by members of FIPA TC A, the Technical Committee of FIPA charged with this work. Other FIPA Technical Committees also made substantial contributions to this effort, and we thank them for their effort and assistance.
2 Scope and Methodology
This section provides a context for the Abstract Architecture, the scope of the work and methodology used in this work.
2.1 Background
FIPA’s goal in creating agent standards is to promote inter-operable agent applications and agent systems. In 1997 and 1998, FIPA issued a series of agent system specifications that had as their goal inter-operable agent systems. This work included specifications for agent infrastructure and agent applications. The infrastructure specifications included an agent communication language, agent services, and supporting management ontologies. There were also a number of application domains specified, such as personal travel assistance and network management and provisioning.
At the heart FIPA’s model for agent systems is agent communication, where agents can pass semantically meaningful messages to one another in order to accomplish the tasks required by the application. In 1998 and 1999 it became clear that it would be useful to support variations in those messages:
· How those messages are transferred (that is, the transport).
· How those messages are represented (as strings, as objects, as XML).
· Optional attributes of those messages, such as how to authenticate or encrypt them.
It also became clear that to create agent systems, which could be deployed in commercial settings, it was important to understand and to use existing software environments. These environments included elements like:
· distributed computing platforms or programming languages,
· messaging platforms,
· security services,
· directory services, and,
· intermittent connectivity technologies.
FIPA was faced with two choices: to incrementally revise specifications to add various features, such as intermittent connectivity, or to take a more holistic approach. The holistic approach, which FIPA adopted in January of 1999, was to create an architecture that could accommodate a wide range of commonly used mechanisms, such as various message transports, directory services and other commonly, commercially available development platforms. For detailed discussions of the goals of the architecture, see:
·
Section
7, Informative
Annex A: Goals of Message Transport
Abstractions.
· Section 8, Informative Annex B: Goals of Directory Service Abstractions.
·
Section
9, Informative
Annex C: Goals for Abstract Agent Communication
Language.
·
Section
10, Informative Annex D: Goals for
Security and Identity Abstractions.
These describe in greater detail the design considerations that were considered when creating this abstract architecture. In addition, FIPA needed to consider the relationship between the existing FIPA 97, FIPA 98 and FIPA 2000 work and the abstract architecture. While more validation is required, the FIPA 2000 work is probably a concrete realization of this abstract architecture. (This validation is required because both the FIPA 2000 and the architecture are not yet complete.) While one of the goals in creating this architecture was to maintain full compatibility with the FIPA 97 and 98 work, this was not entirely feasible, especially when trying to support multiple implementations.
Agents built according to FIPA 97 and 98 specifications will be able to inter-operate with agents built according to the abstract architecture through gateways with some limitations. The FIPA 2000 architecture is a closer match to the abstract architecture, and will be able to fully inter-operate via gateways. The overall goal in this architectural approach is to permit the creation of systems that seamlessly integrate within their specific computing environment while interoperating with agent systems residing in separate environments.
2.2 Why an Abstract Architecture?
The first purpose of this work is to foster interoperability and reusability. To achieve this, it is necessary to identify the elements of the architecture that must be codified. Specifically, if two or more systems use different technologies to achieve some functional purpose, it is necessary to identify the common characteristics of the various approaches. This leads to the identification of architectural abstractions: abstract designs that can be formally related to every valid implementation.
By describing systems abstractly, one can explore the relationships between fundamental elements of these agent systems. By describing the relationships between these elements, it becomes clearer how agent systems can be created so that they are interoperable. From this set of architectural elements and relations one can derive a broad set of possible concrete architectures, which will interoperate because they share a common design.
Because the abstract architecture permits the creation of many concrete realizations, it must provide mechanisms to permit them interoperate. This includes providing transformations for both transport and encodings, as well as integrating these elements with the basic elements of the environment.
For example, one agent system may transmit ACL messages using the OMG IIOP protocol. A second may use IBM’s MQ-series enterprise messaging system. An analysis of these two systems – how senders and receivers are identified, and how messages are encoded and transferred – allows us to arrive at a series of architectural abstractions involving messages, encodings, and addresses.
2.3 Scope of the Abstract Architecture
The primary focus of this abstract architecture is create semantically meaningful message exchange between agents which may be using different messaging transports, different Agent Communication Languages, or different content languages. This requires numerous points of potential interoperability. The scope of this architecture includes:
· Message transport interoperability.
· Supporting various forms of ACL representations.
· Supporting various forms of content language.
· Supporting multiple directory services representations.
It must be possible to create implementations that vary in some of these attributes, but which can still interoperate.
Some aspects of potential standardization are
outside of the scope of this architecture. There are three different reasons
why things are out of scope:
·
The area can not
be describe abstractly.
·
The area is not yet ready for standardization, or there
was not yet sufficient agreement about how to standardize it.
·
The area is
sufficiently specialized that it does not currently need standardization.
Some of the key areas that are not included in this architecture are:
·
Agent lifecycle
and management.
·
Agent mobility.
·
Domains.
·
Conversational
policy.
·
Agent Identity.
The next sections describe the rationale for
this in more detail. However, it extremely important to understand that the
abstract architecture does not prohibit additional features – it merely
addresses how interoperable features should be implemented. It is anticipated
that over time some of these areas will be part of the interoperability of
agent systems.
2.3.1 Areas that are not Sufficiently Abstract
An abstraction may not appear in the abstract architecture because is there is no clean abstraction for different models of implementation. Two examples of this are agent lifecycle management and security related issues.
For example, in examining agent lifecycle, it seems clear there are a minimum set of features that are required: Starting an agent, stopping an agent, “freezing” or “suspending” an agent, and “unfreezing” or “restarting” an agent. In practice, when one examines how various software systems worked, there was very little consistency in the mechanisms used in the different systems, nor in how to address and use those mechanisms. Although it is clear that concrete specifications will have to address these issues, it is not clear how to provide a unifying abstraction for these features. Therefore there are some architectural elements that can only appear at the concrete level, because the details of different environments are so diverse.
Security had similar issues, especially when trying to provide security in the transport layer, or when trying to provide security for attacks that can occur because a particular software environment has characteristics that permits that sort of attack. Agent mobility is another implementation specific model that can not easily be modelled abstractly.
Both of these topics will be addressed in the Instantiation Guidelines, because they are an important part of how agent systems are created. However, they can not be modelled abstractly, and are therefore not included at the abstract level of the architecture.
2.3.2 Areas to be Considered in the Future
FIPA may address a number of areas of agent standardization in the
future. These include domains, conversational policies, mechanisms which are
used to control systems (resource allocation and access control lists), and
agent identity. These all represent ideas which require further development.
This architecture has not addressed application interoperability. The current model for application interoperability is that agents which communicate using a shared set of semantics (such as represented by an ontology) can potentially interoperate. This architecture has not extended that model any further.
2.4 Going From Abstract to Concrete Specifications
This document describes an abstract architecture. Such an architecture cannot be implemented as it stands. Instead the abstract architecture forms the basis for the development of concrete architectural specifications. Such specifications describe in precise detail how to construct an agent system, including the agents and the services that they rely upon, in terms of concrete software artefacts, such as programming languages, applications programming interfaces, network protocols, operating system services, and so forth.
In order for a concrete architectural specification to be FIPA compliant, it must have certain properties. First, the concrete architecture must include mechanisms for agent registration and agent discovery and inter-agent message transfer. These services must be explicitly described in terms of the corresponding elements of the FIPA abstract architecture. The definition of an abstract architectural element in terms of the concrete architecture is termed a realization of that element; more generally, a concrete architecture will be said to realize all or part of an abstraction.
The designer of the concrete architecture has considerable latitude in how he or she chooses to realize the abstract elements. If the concrete architecture provides only one encoding for messages, or only one transport protocol, the realization may simplify the programmatic view of the system. Conversely, a realization may include additional options or features that require the developer to handle both abstract and platform-specific elements. That is to say that the existence of an abstract architecture does not prohibit the introduction of elements useful to make a good agent system, it merely sets out the minimum required elements.
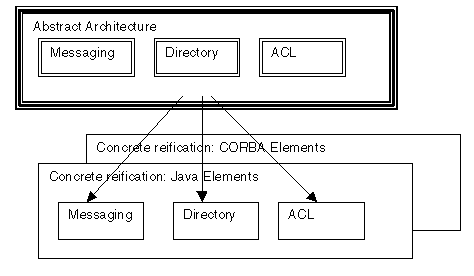
Figure 1: Abstract Architecture Mapped to Various Concrete Realizations
The abstract architecture also describes optional elements. Although an element is optional at the abstract level, it may be mandatory in a particular realization. That is, a realization may require the existence of an entity that is optional at the abstract level (such as a message-transport-service), and further specify the features and interfaces that the element must have in that realization.
It is also important to note that a realization can be of the entire architecture, or just one element. For example, a series of concrete specifications could be created that describe how to represent the architecture in terms of particular programming language, coupled to a sockets based message transport. Messages are handled as objects with that language, and so on.
On the other hand, there may be a single element that can be defined concretely, and then used in a number of different systems. For example, if a concrete specification were done for the directory-service element that describes the schemas to use when it is implemented in LDAP, that particular element might appear in a number of different agent systems.
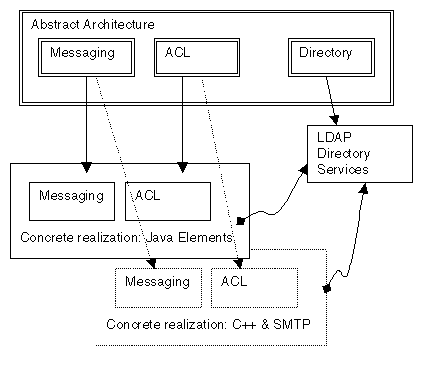
Figure 2: Concrete Realizations Using a Shared Element Realization
In this example, the concrete realization of directory is to implement the directory services in LDAP. Several realizations have chosen to use this directory service model.
2.5 Methodology
This abstract architecture was created by the use of UML modelling, combined with the notions of design patterns as described in Design Patterns (Gamma, Helm, Johnson & Vlissides, Addison-Welsley, 1995). Analysis was performed to consider a variety ways of structuring software and communications components in order to implement the features of an intelligent multi-agent system. This ideal agent system was to be capable exhibiting execution autonomy and semantic interoperability based on an intentional stance. The analysis drew upon many sources:
· The abstract notions of agency and the design features which flow from this.
· Commercial software engineering principles, especially object-oriented techniques, design methodologies, development tools and distributed computing models.
· Requirements drawn from a variety of applications domains.
· Existing FIPA specifications and implementations.
· Agent systems and services, include FIPA and non-FIPA designs.
· Commercially important software systems and services, such as Java, CORBA, DCOM, LDAP, X.500 and MQ Series.
The primary purpose of this work is to foster interoperability and reusability. To achieve this, it is necessary to identify the elements of the architecture that must be codified. Specifically, if two or more systems use different technologies to achieve some functional purpose, it is necessary to identify the common characteristics of the various approaches. This leads to the identification of architectural elements: abstract designs that can be formally related to every valid implementation.
For example, one agent system may transmit ACL messages using the OMG IIOP protocol. A second may use IBM’s MQ-series enterprise messaging system. An analysis of these two systems – how senders and receivers are identified, and how messages are encoded and transferred – allows us to arrive at a series of architectural abstractions involving messages, encodings, and addresses.
In some areas, the identification of common abstractions is essential for successful interoperation. This is particularly true for agent-to-agent message transfer. The end-to-end support of a common agent communication language is at the core of FIPA's work. These essential elements which correspond to mandatory implementation specifications are here described as mandatory architectural elements. Other areas are less straightforward. Different software systems, particularly different types of commercial middleware systems, have specialized frameworks for software deployment, configuration, and management, and it is hard to find common principles. For example, security and identity remain tend to be highly dependent on implementation platforms. Such areas will eventually be the subjects of architectural specification, but not all systems will support them. These architectural elements are optional.
This document models the elements and their relationships. In Section 3, Architectural Overview there is an overview of the architecture. In Section 4, Agent and Agent Information Model there are diagrams in UML notation to describe the relationships between the elements In Section 5, Architectural Elements, each of the architectural elements is described.
2.6 Status of the Abstract Architecture
There are several steps in creating the abstract architecture:
1. Modelling of the abstract elements and their relationships.
2. Representing the other requirements on the architecture that can not be modelled abstractly.
3. Describing interoperability points.
This document represents the first item in the list. It is nearing completion, and ready for review.
The second step is satisfied by guidelines for instantiation. This document will not be written until at least one specification based on the abstract architecture has been created, as it is desirable to base such a document on actual implementation experience.
Interoperability points and conformance are defined by specific interoperability profiles. These profiles will be created as required during the creation of concrete specifications.
3 Architectural Overview
The FIPA architecture defines at an abstract level how two agents can locate and communicate with each other by registering themselves and exchanging messages. To do this, a set of architectural elements and their relationships are described. In this section the basic relationships between the elements of the FIPA agent system are described. In Section 4, Agent and Agent Information Model and Section 5, Architectural Elements, there are UML Models for the architecture, and a detailed description of each element, and its status within the architecture (such as whether it is mandatory or optional).
This section gives a relatively high level description of the notions of the architecture. It does not explain all of the aspects of the architecture. Use this material as an introduction, which can be combined with later sections to reach a fuller understanding of the abstract architecture. There are some terms that are used in this document that should be described. Reserved terms are given in Table 1.
|
Word |
Definition |
|
Actual |
Description of an element. The element relates to actual functionality in the system. Some elements that are explanatory are introduced because they provide a way to group or collect other entities. Some elements are actual, others explanatory Editor’s note: read all the other definitions and then re-read this one. It will make more sense after you read the rest |
|
Can, May |
In relationship descriptions, the word can or may is used to indicate this is an optional relationship. For example, a FIPA-service may provide an API invocation, but it is not required to do so. |
|
Element (or architectural element) |
A member of this abstract architecture. The word element is used here to indicate an item or entity that is part of the architecture, and participates in relationships with other elements of the architecture |
|
Explanatory |
An entity that may not appear in the system. Introduced for the purposes of modelling and clarity, rather than as a likely element of the system. |
|
Functional element |
Description of an element. If this element appears, it can be implemented either as a single software entity or can have its functionality embedded across multiple software entities. For example, a service which provides message transport could be implemented as single entity, or as a set of software that offers things such as a conversation factory, a communication handler, a message tracking and recording service, and so on. As long as this set answers the requirements defined for that element, and the element is defined as functional, then the implementation would be in accordance with the FIPA Architecture. |
|
Mandatory |
Description of an element or relationship. Required in all implementations of the FIPA Abstract Architecture |
|
Must |
In relationship descriptions, the word must is used to indicate this is a mandatory relationship. For example, an agent must have an FIPA-entity-name means that an agent is required to have an FIPA-entity-name. |
|
Optional |
Description of an element or relationship. May appear in any implementation of the FIPA Abstract Architecture, but is not required. Functionality that is common enough that it was included in model. |
|
Realize, realization |
To create a concrete specification or instantiation from the abstract architecture. For example, there may be a design to implement the abstract notion of directory-services in LDAP. This could also be said that there is a realization of directory-services. |
|
Relationship |
A connection between two elements in the architecture. The relationship between two elements is named (for example “is an instance of”, “sends message to”) and may have other attributes, such as whether it is required, optional, one-to-one, or one-to-many. The term as used in this document, is very much the way the term is used in UML or other system modelling techniques. |
|
Single element |
Description of an element or
relationship. If this element
appears, it will be implemented as an identifiable software entity (though it
may be composed of many components). For example, an agent, an directory-entry,
and a FIPA-message are all “single entities” in the system. |
Table 1: Terminology
3.1 FIPA Entities, FIPA Services and Agents
One of the basic building blocks of the FIPA agent model is the FIPA-entity. FIPA-entities are named entities in the FIPA architecture. In this version of the Abstract Architecture, there is only one type of FIPA-entity: the agent. The abstraction FIPA-entity is introduced in order to provide a smooth transition to future versions of the architecture in which entities other than agents may be named.
Agents communicate by exchanging messages which represent speech acts, and which are encoded in an agent-communication-language.
FIPA-services provide support services for agents. This version of the abstract architecture defines two support services: directory-services and message-transport-services.
FIPA-services may be implemented either as agents or as software that is accessed via method invocation, using programming interfaces such as those provided in Java, C++, or IDL. An agent providing a FIPA-service is more constrained in its behaviour than a general purpose agent. In particular, these agents are required to preserve the semantics of the service. This implies that these agents do not have the degree of autonomy normally attributed to agents. They may not arbitrarily refuse to provide the service.
When implementing the Abstract Architecture, a FIPA-entity will not necessarily be mapped to a single feature of the implementation. It is an element that simply serves as a useful abstraction in describing the architecture.
3.2 Directory Services
The basic role of the directory-service function is to provide a place where FIPA-entities (agents) register directory-entries. Other agents can search the directory-entries to find agents with which they wish to interact.
The directory-entry consists of:
|
FIPA-entity-name |
A
unique name for the FIPA-entity (agent) |
|
Locator |
One or more transport-descriptors that describe the transport-type and the transport-specific-address to use to communicate with that agent |
|
FIPA-entity-attributes |
Optional descriptive attributes, such as what services the FIPA-entity offers, cost associated with using the FIPA-entity, restrictions on using the FIPA-entity, etc.. Represented as keyword and value pairs. |
3.2.1 Starting an Agent
Agent A wishes to advertise itself as a provider of some service. It first binds itself to one or more transports. In some implementations it will delegate this task to the message-transport-service; in others it will handle the details of, for example, contacting an ORB, or registering with an RMI registry, or establishing itself as a listener on a message queue. As a result of these actions, the agent is addressable via one or more transports.
Having established one or more transport mechanisms, the agent must advertise itself. It does this by constructing an directory-entry and registering it with the directory-service. The directory-entry includes the agent’s name, its transport addressing information, and a set of properties that describe the service. A stock service might advertise itself as “agent-service com.dowjones.stockticker” and “ontology org.fipa.ontology.stockquote”.
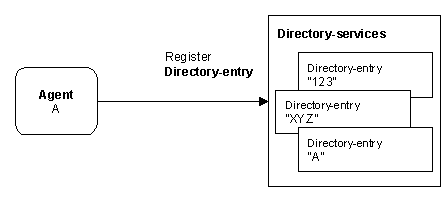
Figure 3: An Agent Registers with a Directory Service
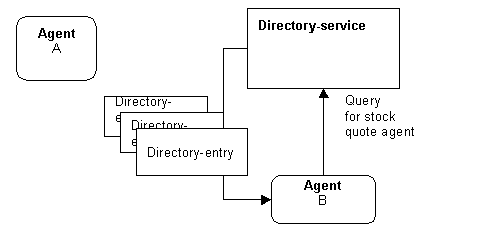
3.2.2 Finding an Agent
Agents can use the directory-service to locate agents with which to communicate. If agent B is seeking stock quotes, it may search for an agent that uses the ontology “org.fipa.ontology.stockquote”. If it does so, it will retrieve the directory-entry for agent A. It might also retrieve other directory-entries for agents that support that ontology.
Figure 4: Directory Query
Agent B can then examine the directory-entries to determine which agent best suits its needs. The directory-entries include the FIPA-entity-name, the locator, which contains information related to how to communicate with the agent, and other attributes.
3.2.3 Starting a FIPA Service
In some implementations, a FIPA-service is implemented as an agent. In such cases, the process of starting a FIPA-service is similar to starting an agent. When a FIPA-service starts, it may bind itself to a particular message-transport-service. It then registers with the directory-service, supplying a directory entry. This permits agents and FIPA-services to find the service through directory query.
In other implementations, a FIPA-service is accessed via a programmatic interface in a language such as Java, C++ or IDL. In these cases, the issues of starting, finding, and registering the service are not relevant.
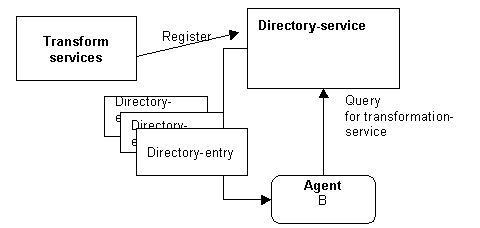
Figure 5: Directory Query for a Service
3.3 Agent Messages
In FIPA agent systems agents communicate with one another, by sending messages. Here are some basic notions about agents messages, and their communications. There are two aspects of the messages passed between agents: the structure of the message itself, and the message when it is being prepared to be sent over a particular transport.
3.3.1 Message Structure
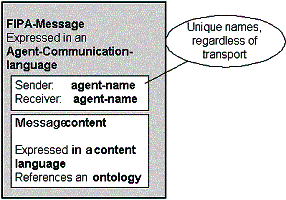
The basic message unit is the FIPA-message. A FIPA-message is written in an agent-communication-language, such as FIPA ACL. The content of the FIPA-message is expressed in a content-language, such as KIF or SL. The content-language may reference an ontology, which grounds the concepts being discussed in the content. The FIPA-messages also contains the sender and receiver names, expressed as FIPA-entity-names. FIPA-entity-names are unique names for an agent.
FIPA-messages can contain other FIPA-messages.
3.3.2 Message Transport
When a FIPA-message is sent it is transformed into a payload, and included in a transport-message. A payload is the message-encoding-representation appropriate for the transport. For example, if the message is going to be sent over a low bandwidth transport (such a wireless connection) a bit efficient representation may used instead of a string representation to allow more efficient transmission.
The transport-message is the payload plus the envelope. The envelope includes the sender and receiver transport-descriptions. The transport-descriptions contain the information about how to send the message (via what transport, to what address, with details about how to utilize the transport). The envelope can also contain additional information, such as the message-encoding-representation, data related security, and other realization specific data that needs be visible to the transport or recipient.
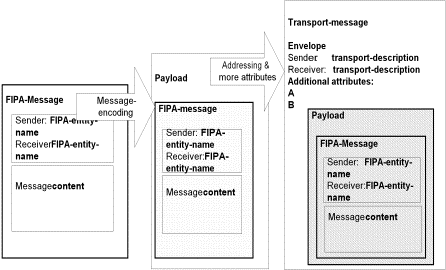
Figure 7: A FIPA-message Becomes a transport-message
In the above diagram, a FIPA-message is transformed into a payload suitable transport over the selected message-transport. An appropriate envelope is created that has sender and receiver information that uses the transport-description data appropriate to the transport selected. There may be additional envelope data included as well. The combination of the payload and envelope is a transport-message.
3.4 Agents Send Messages to Other Agents
In FIPA agent systems agents communicate with one another. Here are some basic notions about agents, and their communications.
Each agent
has an FIPA-entity-name. This FIPA-entity-name is unique and
unchangeable. Each agent also has
one or more transport-descriptions,
which are used by other agents to send a transport-message.
Each transport-description
correlates to a particular form of message transport,
such as IIOP, SMTP, or HTTP. A transport
is a mechanism for transferring messages. A
transport-message is a message that sent from one agent to another in a
format (or encoding) that is appropriate to the transport being used. A set
of transport-descriptions can be
held in an locator.
For example, there may be an agent with the FIPA-entity-name “ABC”. This agent is addressable through two different transports, HTTP, and an SMTP e-mail address. Therefore, agent has two transport-descriptions, which are held in the locator. The transport descriptions are as follows.
Directory entry for ABC
FIPA-entity-name: ABC
Locator:
|
Transport-type
|
Transport-specific-address |
Transport-specific-property |
|
HTTP |
http://www.whiz.net/abc |
(none) |
|
SMTP |
Abc@lowcal.whiz.net |
(none) |
FIPA-entity-attributes: Attrib-1: yes
Attrib-2: yellow
Language: French, German, English
Preferred negotiation: contract-net
Note: in this example, the FIPA-entity-name is used as part of the transport-descriptions. This is just to make these examples easier to read. There is no requirement to do this.
Another agent can communicate with agent “ABC” using either transport-description, and know that which agent it is communicating with. In fact, the second agent can even change transports and can continue its communication. Because the second agent knows the FIPA-entity-name, it can retain any reasoning it may be doing about the other agent, without loss of continuity.
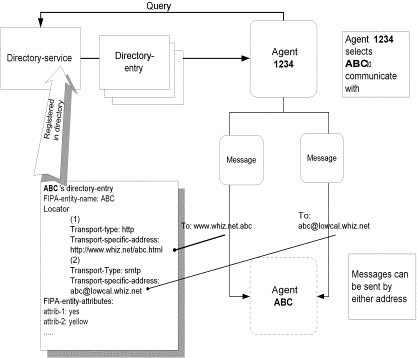
Figure 8: Communicating Using Any Transport
In the above diagram, Agent 1234 can communicate with Agent ABC using either an SMTP transport or an HTTP transport. In either case, if Agent 1234 is doing any reasoning about agents that it communicates with, it can use the FIPA-entity-name “ABC” to record which agent it is communicating with, rather than the transport description. Thus, if it changes transports, it would still have continuity of reasoning.
Here’s what the messages on the two different transports might look like:
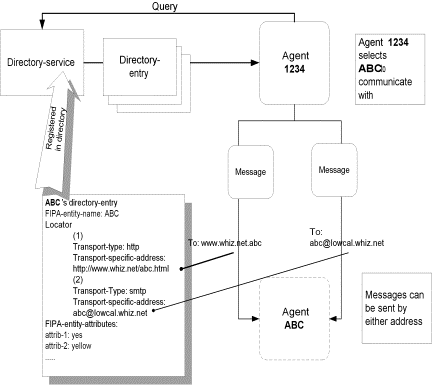
Figure 9: Two transport-messages to the Same Agent
In the diagram above, the transport-description is different, depending on the transport that is going to be used. Similarly, the message-encoding of the payload may also be different. However, the FIPA-entity-names remain consistent across the two message representations.
3.5 Providing Message Validity and Encryption
There are many aspects of security that can be provided in agent systems. See Section 10, Informative Annex D: Goals for Security and Identity Abstractions for full discussion of possible security features. In this abstract architecture, there is a simple form of security: message validity and message encryption. In message validity, messages can be sent in such a way that it possible to determine the message has not been modified during transmission. In message encryption, a message is sent in such a way that the message itself is encrypted, so that the message content can not be read by others.
In this abstract architecture, these are accommodated through message-encoding-representations and the use of additional attributes in the envelope. For example, as the payload is transformed, one of the transforms might be to a digitally encrypted set of data, using a public key and particular encryption algorithm. Additional parameters are added to the envelope to indicate these characteristics.
Therefore, the creation message validation and encryption is treated like any other type message transformation.
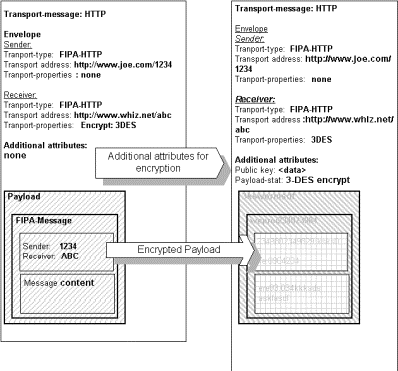
Figure 10: Encrypting a Message Payload
In the above diagram, the payload is encrypted, and additional attributes are added to the envelope to support the encryption. Those attributes must not be encrypted, or the receiving party would not be able to use them.
3.6 Providing Interoperability
There are several ways in which the abstract architecture intends to provide interoperability. The first is transport interoperability. The second is message representation interoperability.
To provide interoperability, there are certain elements that must be included throughout the architecture to permit multiple implementations. For example, earlier, it was described that an agent has both an FIPA-entity-name and a locator. The locator contains transport-descriptions, each of which contains information necessary for a particular transport to send a message to the corresponding agent. The semantics of agent communication require that an agent’s name be preserved throughout its lifetime, regardless of what transports may be used to communicate with it.
4 Agent and Agent Information Model
This section of the abstract architecture provides a series of UML class diagrams for key elements of the abstract architecture. In Section 5, Architectural Elements you can get a textual description of these elements and other aspects of the relationships between them. In order to make these diagrams more readable, certain elements are included in multiple diagrams.
Comment on notation: In UML, the notion of a 1 to many or 0 to many relationship is often noted as “1…*” or “0…*”. The tool that was used to generate these diagrams used the convention “1…n” and “0…n” to express the concept of many. The diagrams use the “n” style notation.
4.1 Agent Relationships
The following UML diagram outlines the basic relationships between an agent and other key elements of the FIPA abstract architecture. In other diagrams in this section you can get details on the locator, and the transport-message.
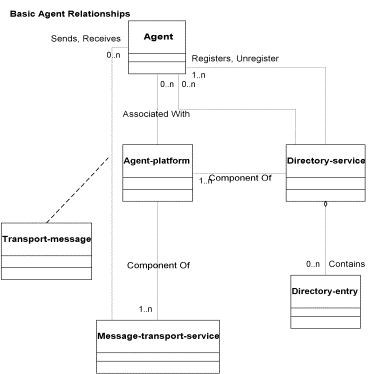
Figure 11: UML - Basic Agent Relationships
4.2 Transport Message Relationships
Transport-message is the object conveyed from agent to agent. It contains the transport-description for the sender and receiver or receivers, together with a payload containing the FIPA-message.

Figure 12: UML - Transport Message Relationships
4.3 Directory Entry Relationships
The directory-entry contains the FIPA-entity-name, locator and FIPA-entity-attributes. The locator provides ways to address messages to an agent. It is also used in modifying transport requests.
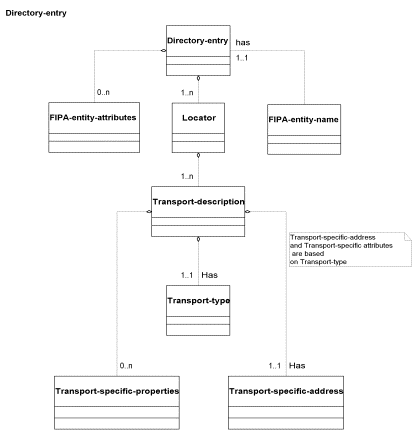
Figure 13: UML - Directory-entry and locator Relationships
4.4 FIPA Message Elements
This diagram shows the elements in a FIPA-message. A FIPA-message is contained in a transport-message when messages are sent.
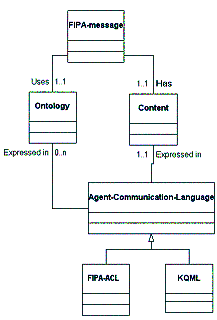
Figure 14: UML - FIPA-message Elements
4.5 Message Transport Elements
The message-transport-service is an option service that can send transport-messages between agents. These elements may participate in other relationships as well.
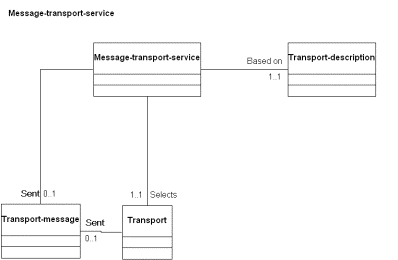
Figure 15: UML - Message Transport Entities
4.6 FIPA Entity Relationships
The following UML diagram describes the FIPA-entity relationships. A FIPA-entity is an addressable software component that delivers some of functionality of the abstract architecture.
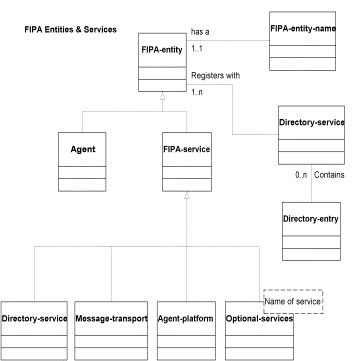
Figure 16: UML - FIPA Entity Relationships
5 Architectural Elements
The architectural elements are defined here. For each element, the semantics are described informally. Then the relationships between the element and other elements are defined.
5.1 Introduction
5.1.1 Classification of Elements
The word element is used here to indicate an item or entity that is part of the architecture, and participates in relationships with other elements of the architecture.
The architectural elements are classified in three ways. Firstly, they are classified as mandatory or optional. Mandatory elements must appear in all instantiations of the FIPA abstract architecture. They describe the fundamental services, such as agent registration and communications. These elements are the core aspects of the architecture. Optional elements are not mandatory; they represent architecturally useful features that may be shared by some, but not all, concrete instantiations. The abstract architecture only defines those optional elements which are highly likely to occur in multiple instantiations of the architecture.
The second classification is whether elements are actual or explanatory. Actual elements must be created as a software that meets the required functionality. They may be either mandatory or optional. Explanatory elements exist simply as useful constructs in the system, such as gathering together similar elements. For example, there is an explanatory entity, FIPA-service, which contains attributes that all FIPA-services should have. However, there is no independent entity, FIPA-service. Instead, there are various services, such as message-transport-service and directory-service, that inherit characteristics from that element.
The third classification is whether the element must be implemented as a single software entity, or if the functionality can be spread across multiple entities. Note that a single software entity may be in turn composed of several components, but functionality there is a mechanism that makes that entity addressable (for example, it can accept messages, has an API, or something similar). These are said to be single or functional elements
|
Type |
Definition |
|
Mandatory |
Required in any implementation of the FIPA Abstract Architecture |
|
Optional |
May appear in any implementation of the FIPA Abstract Architecture. Functionality that is common enough that it was included in model |
|
Actual |
Relates to actual functionality in the system. Some elements that are explanatory are introduced because they provide a way to group or collect other entities |
|
Explanatory |
An entity that may not appear in the system. Introduced for the purposes of modelling and clarity, rather than as a likely element of the system. |
|
Single Entity |
If this element appears, it will be implemented as an identifiable software entity (though it may be composed of many components). For example, an agent, an directory-entries, and a FIPA-message are all “single entities” in the system. |
|
Functional |
If this element appears, it can be implemented either as a single software entity or can have its functionality embedded across multiple software entities. For example, a service which provides message transport could be implemented as single entity, or as a set of software that offers things such as a conversation factory, a communication handler, a message tracking and recording service, and so on. As long as this set answers the requirements defined for that element, and the element is defined as functional, then the implementation would be in accordance with the FIPA Architecture. |
Table 2: Categorization of Elements
5.1.2 Key-Value Tuples
Many of the elements of the abstract architecture are defined to be key-value tuples, or KVTs. The concept of a KVT is central to the notion of architectural extensibility, and so it is discussed in some length here.
A KVT consists of an unordered set of key-value pairs. Each key-value pair has two elements, as the term implies. The first element, the key, is a token drawn from an administered name space. All keys defined by the Abstract Architecture are drawn from a name space managed by FIPA. This makes it possible for concrete architectures, or individual implementations, to add new architectural elements in a manner which is guaranteed not to conflict with the Abstract Architecture.
The second element of the key-value pair is the value. The type of value depends on the key; in some concrete specifications this type may correspond to a type in some programming language or object model.
5.1.3 Services
A FIPA-service is defined in terms of a set of actions which it supports. Each action defines an interaction between the service and the FIPA-entity which is using the service. The semantics of these actions are described informally, to minimize assumptions about how they might be reified in a concrete specification.
5.1.4 Format of Element Description
The architectural elements are described below. The format of the description is:
· Summary. A summary of the element.
· Relationship to other elements. A complete description of the relationship of this element to the other architectural elements.
· Relationship to concrete specification. Whether this is a mandatory or optional element, and whether the element is actual or explanatory in a concrete instantiation. There may be additional comments related to making this element concrete.
· Description. Additional description and context for the element, along with explanatory notes and examples.
5.1.5 Abstract Elements
|
Element |
Description |
Mandatory Optional |
Actual Explanatory |
Single
or Functional
Element |
|
Action-status |
An indication delivered by a service indicating the success or failure of an action |
Mandatory |
Actual |
Functional |
|
Agent |
Computational process that implements the autonomous, communicating functionality of an application |
Mandatory |
Actual |
Single |
|
Agent-communication-language |
Language with a precisely defined syntax
semantics and pragmatics, which is the basis of communication between
independently designed and developed agents. |
Mandatory |
Actual |
Functional |
|
Content |
Content is that part of a communicative act that represents the domain dependent component of the communication. |
Mandatory |
Actual |
? |
|
Content-language |
A language used to express the content of a communication between agents. |
Mandatory |
Actual |
Single |
|
Directory-entry |
A composite entity containing the name, locator, and FIPA-entity-attributes of a FIPA-entity |
Mandatory |
Actual |
Single |
|
Directory-service |
A FIPA-service providing a shared information repository in which directory-entries may be stored and queried |
Mandatory |
Actual |
Single |
|
Envelope |
That part of a transport-message which contains information about how to send the message to the intended recipients. May also include additional information about the message encoding, encryption, and so on. |
Mandatory |
Actual |
Single |
|
Explanation |
An encoding of the reason for a particular action-status. |
Optional |
Actual |
Single |
|
FIPA-entity |
A FIPA-entity is a software component that delivers a portion of the functionality of the abstract architecture. |
Optional |
Explanatory |
N/A |
|
FIPA-entity-attributes |
A set of properties associated with a FIPA-entity by inclusion in its directory-entry |
Optional |
Actual |
Single |
|
FIPA-entity-name |
An opaque, non-forgeable token which uniquely identifies a FIPA-entity (agent) |
Mandatory |
Actual |
Single |
|
FIPA-message |
A unit of individual communication between two agents. The FIPA-Message is expressed in agent-communication-language, and is encoded in a particular message-transport-encoding. |
Mandatory |
Actual |
Single |
|
FIPA-service |
A service provided for agents and other FIPA-services |
Optional |
Explanatory |
N/A |
|
Locator |
A locator consists of the set of transport-descriptions which can be used to communicate with a FIPA-entity (agent) |
Mandatory |
Actual |
Single |
|
Message-encoding-representation |
A way of representing an abstract syntax in a particular concrete syntax. Examples of possible representations are XML, FIPA strings, and serialized Java objects. |
Mandatory |
Actual |
Functional |
|
Message-transport-service |
A FIPA-service that supports the sending and receiving of transport-messages between agents. |
Optional |
Actual |
Functional |
|
Ontology |
A set of symbols together with an associated interpretation that may be shared by a community of agents or software. An ontology includes a vocabulary of symbols referring to objects in the subject domain, as well as symbols referring to relationships that may be evident in the domain |
Mandatory |
Actual |
Functional |
|
Payload |
A FIPA-message encoded in a manner suitable for inclusion in a transport-message. |
Mandatory |
Actual |
Single |
|
Transport |
A transport
is a particular data delivery service which is supported by a message-transport-service |
Mandatory |
Actual |
Functional |
|
Transport-description |
A transport-description is a self describing structure containing a transport-type, a transport-specific-address and zero or more transport-specific-properties |
Mandatory |
Actual |
Single |
|
Transport-message |
The object conveyed from agent to agent. It contains the transport-description for the sender and receiver or receivers, together with a payload containing the FIPA-message. |
Mandatory |
Actual |
Single |
|
Transport-specific-property |
A transport-specific-property is a property associated with a transport-type. |
Optional |
Actual |
Single |
|
Transport-type |
A transport-type describes the type of transport which is associated with an transport-specific-address. |
Mandatory |
Actual |
Single |
Table 3: Abstract Elements
5.2 Agent
5.2.1 Summary
An agent is a computational process that implements the autonomous, communicating functionality of an application. Typically, agents communicate using an Agent Communication Language.
5.2.2 Relationships to Other Elements
Agent is an instance of FIPA-entity
Agent may have an locator, which lists the transport-descriptions for that agent
Agent may be sent messages via a transport-description, using the transport corresponding to the transport-description
Agent may send a transport-message
to one or more agents
Agent
may register with one or more directory-services
Agent
may have an
directory-entry, which is registered with a directory-service
Agent may modify its directory-entry as registered by a directory-service
Agent may delete its directory-entry from a directory-service.
Agent may query for an directory-entry
registered within a directory-service
5.2.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Single |
5.2.4 Description
In a concrete instantiation of the abstract architecture, an agent may be realized in a variety of ways: as a JavaÔ component, a COM object, a self-contained Lisp program, or a TCL script. It may execute as a native process on some physical computer under an operating system, or be supported by an interpreter such as a Java Virtual Machine or a TCL system. The relationship between the agent, its computational context, is specified by the agent lifecycle. The abstract architecture does not address the lifecycle of agents, because of it is handled so differently in different computational environments. Realizations of the abstract architecture must address these issues.
Since an agent is a FIPA-entity, it inherits the attributes of a FIPA-entity, in particular a FIPA-entity-name, which identifies the agent uniquely
5.3 Agent Communication Language
5.3.1 Summary
An agent-communication-language (ACL) is a language in which communicative acts can be expressed. The FIPA architecture is defined in terms of an Abstract ACL, or AACL. Any abstract language must have a written form, however it may be that no deployed systems and ACLs use that written notation. Instead, it is required that any given ACL can be seen as a realization of the abstract ACL.
An abstract syntax is a syntax in which the underlying operators and objects of a language are exposed; together with a precise semantics for those entities. When specifying an abstract syntax it inevitably becomes “concrete” by virtue of the fact that it has been written down as characters and tokens. However, generally, written abstract syntaxes are still simpler and have far fewer features than their concrete cousins. The primary role of an abstract syntax is to facilitate focussing on the meaning of constructs in the language at the possible expense of legibility and convenience of expression.
5.3.2 Relationships to Other Elements
FIPA-message is written in an agent-communication-language.
5.3.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Functional |
5.3.4 Description
???
5.4 Content
5.4.1 Summary
Content is that part of a communicative act that represents the component of the communication that refers to a domain or topic area. Note that "the content of a message" does not refer to "everything within the message, including the delimiters", as it does in some languages, but rather specifically to the domain specific component. In the ACL semantic model, a content expression may be composed from propositions, actions or terms.
5.4.2 Relationships to Other Elements
Content is expressed in a content-language
Content may reference one or more ontologies
Content is part of a FIPA-message
5.4.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Single |
5.5 Content Language
A content-language is a language used to express the content of a communication between agents. FIPA allows considerable flexibility in the choice and form of a content language; however, content languages are required to be able to represent propositions, actions and terms (names of individual entities) if they are to make full use of the standard FIPA performatives.
5.5.1 Relationships to Other Elements
Content is expressed in a content-language
FIPA-SL is an example of a content-language
FIPA-RDF is an example of a content-language
FIPA-KIF is an example of a content-language
FIPA-CCL is an example of a content-language
5.5.2 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Single |
5.5.3 Description
The FIPA 2000 content languages are described in detail in [FIPA00007].
5.6 Directory Entry
5.6.1 Summary
An directory-entry is a key-value tuple consisting of the FIPA-entity-name, a locator, and zero or more FIPA-entity-attributes. A directory-entry refers to an agent; in some implementations this agent will provide a FIPA-service.
5.6.2 Relationships to Other Elements
Directory-entry contains the FIPA-entity-name of the FIPA-entity to which it refers
Directory-entry contains one locator of the FIPA-entity to which it refers. The locator contains one or more transport-descriptions
Directory-entry is available from a directory-service
Directory-entry contains FIPA-entity-attributes
5.6.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Single |
5.6.4 Description
Different realizations that use a common directory-service, are strongly encouraged to adopt a common schema for storing directory-entries. (This in turn implies the use of a common representation for locators, transport-descriptions, FIPA-entity-names, and so forth.)
Agents are not required to publish an directory-entry. It is possible for agents to communicate with agents that have provided an transport-description through a private mechanism. For example, an agent involved in a negotiation may receive a transport-description directly from the party with which it is are negotiating. This falls outside the scope of the using the directory-services mechanisms.
5.7 Directory Service
5.7.1 Summary
A directory-service is a shared information repository in which agents may publish their directory-entries and in which they may search for directory-entries of interest.
5.7.2 Relationships to Other Elements
Agent may register its directory-entry with a directory-service.
Agent may modify its directory-entry as registered by a directory-service.
Agent may delete its directory-entry from a directory-service.
Agent may search for an directory-entry registered within a directory-service.
A directory-service must accept request for registering, de-registering, deletion, and modification of agent descriptions.
A directory-service must accept requests for searching.
A directory-service is a FIPA-entity.
5.7.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Single |
5.7.4 Actions
A directory-service supports the following actions.
5.7.4.1 Register
An agent may register a directory-entry with a directory-service. The semantics of this action are as follows:
The agent provides a directory-entry which is to be registered. In initiating the action, the agent may control the scope of the action. Different reifications may handle this in different ways. The action may be addressed to a particular instance of a directory-service, or the action may be qualified with some kind of scope parameter.
If the action is successful, the directory-service will return an action-status indicating success. Following a successful register, the directory-service will support legal modify, delete, and query actions with respect to the registered directory-entry.
If the action is unsuccessful, the directory-service will return an action-status indicating failure, together with an explanation. The range of possible explanations is, in general, specific to a particular reification. However a conforming reification must, where appropriate, distinguish between the following explanations:
· Duplicate – the new entry “clashed” with some existing directory-entry. Normally this would only occur if an existing directory-entry had the same FIPA-entity-name, but specific reifications may enforce additional requirements.
· Access – the agent making the request is not authorized to perform the specified action.
· Invalid – the directory-entry is invalid in some way.
5.7.4.2 Modify
An agent may modify a directory-entry which has been registered with a directory-service. The semantics of this action are as follows:
The agent provides a directory-entry which contains the same FIPA-entity-name as the entry which is to be modified. In initiating the action, the agent may control the scope of the action. Different reifications may handle this in different ways. The action may be addressed to a particular instance of a directory-service, or the action may be qualified with some kind of scope parameter.
The directory service verifies that the argument is a valid directory-entry (Dn). It then searches for a registered directory-entry with the same FIPA-entity-name (Dx). If it does not find one, the action fails. Otherwise it modifies Dx by examining each key-value pair in Dn. If the value is non-null, the pair is added to Dx, replacing any existing pair with the same key. If the value is null, any existing pair in Dx with the same key is removed from Dx.
If the action is successful, the directory-service will return an action-status indicating success, together with a directory-entry corresponding to the new contents of the registered entry. Following a successful register, the directory-service will support legal modify, delete, and query actions with respect to the modified directory-entry.
If the action is unsuccessful, the directory-service will return an action-status indicating failure, together with an explanation. The range of possible explanations is, in general, specific to a particular reification. However a conforming reification must, where appropriate, distinguish between the following explanations:
· Not-found – the new entry did not match any existing directory-entry. This would only occur if no existing directory-entry had the same FIPA-entity-name.
· Access – the agent making the request is not authorized to perform the specified action.
· Invalid – the new directory-entry is invalid in some way.
5.7.4.3 Delete
An agent may delete a directory-entry from a directory-service. The semantics of this action are as follows:
The agent provides a directory-entry which has the same FIPA-entity-name as that which is to be deleted. (The rest of the directory-entry is not significant.) In initiating the action, the agent may control the scope of the action. Different reifications may handle this in different ways. The action may be addressed to a particular instance of a directory-service, or the action may be qualified with some kind of scope parameter.
If the action is successful, the directory-service will return an action-status indicating success. Following a successful delete, the directory-service will no longer support modify, delete, and query actions with respect to the registered directory-entry.
If the action is unsuccessful, the directory-service will return an action-status indicating failure, together with an explanation. The range of possible explanations is, in general, specific to a particular reification. However a conforming reification must, where appropriate, distinguish between the following explanations:
· Not-found – the new entry did not match any existing directory-entry. This would only occur if no existing directory-entry had the same FIPA-entity-name.
· Access – the agent making the request is not authorized to perform the specified action.
· Invalid – the directory-entry is invalid in some way.
5.7.4.4 Query
An agent may query a directory-service to locate directory-entries of interest. The semantics of this action are as follows:
The agent provides a directory-entry which is to be treated as a search pattern. In initiating the action, the agent may control the scope of the action. Different reifications may handle this in different ways. The action may be addressed to a particular instance of a directory-service, or the action may be qualified with some kind of scope parameter.
The directory service verifies that the argument is a valid directory-entry (Dp). It then searches for registered directory-entries which satisfy Dp. A registered entry, Dx, satisfies Dp if for each key-value pair in Dp there is a pair in Dx with the same key and a matching value. The semantics of “matching” are likely to be reification-dependent; at a minimum, there should be support for matching on the same value and matching on any value.
If the action is successful, the directory-service will return an action-status indicating success, together with a set of directory-entries which satisfy the search pattern. The mechanism by which multiple entries are returned, and whether or not an agent may limit or terminate the delivery of results, is not defined in the abstract architecture.
If the action is unsuccessful, the directory-service will return an action-status indicating failure, together with an explanation. The range of possible explanations is, in general, specific to a particular reification. However a conforming reification must, where appropriate, distinguish between the following explanations:
· Not-found – the search pattern did not match any existing directory-entry.
· Access – the agent making the request is not authorized to perform the specified action.
·
Invalid – the directory-entry is invalid in some way.
5.7.5 Description
A directory-service may be implemented in a variety of ways, using a general-purpose scheme such as X.500 or some private agent-specific mechanism. Typically a directory-service uses some hierarchical or federated scheme to support scalability. A concrete implementation may support such mechanisms automatically, or may require each agent to manage its own directory usage.
Different realizations that are based on the same underlying mechanism are strongly encouraged to adopt a common schema for storing directory-entries. This in turn implies the use of a common representation for destinations, names, and so forth. For example, if there are multiple implementations for directory service in LDAP, it would be use for all of the implementation to interoperate because they are using the same schemas. Similarly, if there were multiple implementations in NIS, they would need the same NIS data representation to interoperate.
5.8 Envelope
5.8.1 Summary
An envelope is a key-value tuple which contains message delivery and encoding information. It is included in the transport-message, and includes elements such as the sender and receivers transport-descriptions. It also contains the message encoding representation for the FIPA-message included in the message. It optionally contains other message information, such as validation and security data, or additional routing date.
5.8.2 Relationship to Other Elements
Envelope contains transport-descriptions
Envelope optionally contains validity data (such as keys for message validation)
Envelope optionally contains security data (such as keys for message encryption or decryption)
Envelope optionally contains routing data)
Envelope contains message-encoding-representation for the payload being transported
Envelope is contained in transport-message.
5.8.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Single |
5.8.4 Description
In the realization of
the envelope data, the realization can specify envelope elements that are
useful in the particular realization. These can include specialized routing
data, security related data, or other data which can assist in the proper
handling of the encoded FIPA-message.
5.9 FIPA Entity
5.9.1 Summary
A FIPA-entity is a software component that delivers a portion of the functionality of the abstract architecture. There is one types of FIPA-entity: agents.
Note: In a previous version of this document, FIPA-services were also considered to by FIPA-entities. However the requirement that a FIPA-entity be registered in a directory-service and be addressable in terms of its transport-descriptions means that such an abstract relationship is not generally applicable.
5.9.2 Relationships to Other Elements
FIPA-entity has a FIPA-entity-name.
FIPA-entity is registered in the directory-service, using a directory-entry.
FIPA-entity is addressable by the
mechanisms described in its
transport-descriptions in its directory-entry.
FIPA-entity may have FIPA-entity-attributes
5.9.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Explanatory |
N/A |
5.9.4 Description
FIPA-entity is an abstraction introduced to allow for a future generalization. In this version of the architecture, a FIPA-entity is essentially an agent.
5.10 FIPA Entity Attributes
5.10.1 Summary
The FIPA-entity-attributes are optional attributes that are part of the directory-entry for a FIPA-entity. They are represented as a key/value pairs within the key-value tuple that makes up the directory-entry. The purpose of the attributes is to allow searching for directory-entries that match FIPA-entities of interest.
5.10.2 Relationships to Other Elements
A directory-entry may have zero or more FIPA-entity-attributes
FIPA-entity-attributes describe aspects of a FIPA-entity
5.10.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Optional |
Actual |
Single |
5.10.4 Detailed Description
When a FIPA-entity registers a directory-entry, the directory-entry may optionally contain key and value pairs that offer additional description of the FIPA-entity. The values might include information about costs of using the agent or FIPA-service, features available, ontologies understood, or any other data that FIPA-entities deem useful, or names that the service is commonly known by. Other FIPA-entities can then search in the directory service for FIPA-entities that meet particular requirements.
In practice, when defining realizations of this abstract architecture, domain specific specifications should existing about the FIPA-entity-attributes that are going to be presented, to allow for interoperation.
5.11 FIPA Entity Name
5.11.1 Summary
An FIPA-entity-name is a means to identify a FIPA-entity to agents and FIPA-services. It is unchanging (that is, it is immutable) and unique under normal circumstances of operation.
5.11.2 Relationships to Other Elements
FIPA-entity has one FIPA-entity-name
FIPA-message must contain the FIPA-entity-names of the sending and receiving agents
Directory-entry must contain the FIPA-entity-name of the FIPA-entity to which it refers
5.11.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Single |
5.11.4 Description
An FIPA-entity-name is an identifier (a GUID, globally unique identifier) that is associated with the FIPA-entity when it is created or when it registers for the first time. Name issuing should occur in a way that tends to ensure global uniqueness. That is, names should be issued using an algorithm that generates the name in such a way and with a sufficient number of random bits that there is a vanishingly small chance of a name collision.
The FIPA-entity-name will typically be issued by another entity or service. Once issued, the unique identifier should not be dependent upon the continued existence of the third party that issued it. Ideally, there will be an ongoing mechanism to verify the authenticity of the name.
Beyond this durable relationship with the FIPA-entity it denotes, the FIPA-entity-name should have no semantics. It should not encode any actual properties of the agent itself, nor should it disclose related information such as agent transport-description or location. It also should not be used as a form of authentication of the agent. Authentication services must rely on the combination of a unique identifier plus something else (for example, a certificate that makes the name tamper-proof and verifies its authenticity through a trusted third party).
A useful role of an FIPA-entity-name is to support the use of BDI (belief/desire/intention) models within a multi-agent system. The agent name can be used to correlate propositional attitudes with the particular agents that are believed to hold those attitudes.
FIPA-entities, and particularly agents, may also have “well-known” or “common” or “social” names, or “nicknames”, by which they are popularly known. These names are often used to commonly identify an agent. For example, within an agent system, there may be a broker service for finding airfare agents. The convention within this system is that this agent is nicknamed “Air-fare broker”. In practice, this is implemented as a FIPA-entity-attribute (that is there is additional attribute for the agent). The attribute could be “Nickname” and the value for that is “Air-fare broker”. However, the actual name of the agent that is providing the function is unique, so that is possible to distinguish between an agent providing that function in one cluster of agents, and another agent providing the same function in a different cluster of agents.
5.12 FIPA Message
5.12.1 Summary
A FIPA-message is an individual unit of communication between two or more agents. A message corresponds to a communicative act, in the sense that a message encodes the communicative. Communicative acts can be recursively composed, so while the outermost act is directly encoded by the message, taken as a whole a given message may represent multiple individual communicative acts. FIPA-messages are transmitted between agents over a transport.
A FIPA-message includes an indication of the type of communicative act (for example, INFORM, REQUEST), the agent-names of the sender and receiver agents, the ontology to be used in interpreting the content, and the content of the message.
A FIPA-message does not include any transport or addressing information. It is transmitted from sender to receiver by being encoded as the payload of a transport-message, which includes this information.
5.12.2 Relationships to other elements
FIPA-message is written in an agent-communication-language
FIPA-message has content
FIPA-message has an ontology
FIPA-message includes an agent-name corresponding to the sender of the message
FIPA-message includes one or more agent-name corresponding to the receiver or receivers of the message
FIPA-message is sent by an agent
FIPA-message is received by one or more agents
FIPA-message is transmitted as the payload
of a transport-message
5.12.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Single |
5.12.4 Description
???
5.13 FIPA Service
5.13.1 Summary
A FIPA-service is a functional coherent set of mechanisms which support the operation of agents, and other FIPA-services. These are services which are used in the provisioning of Agent Environments and may be used as the basis for interoperation.
5.13.2 Relationships to Other Elements
FIPA-service has a public set of behaviours
FIPA-service has a service description
FIPA-service can be accessed by Agents
Directory-Service is an instance of FIPA-service, and is mandatory
Message-transport-service is an instance of FIPA-service, and is optional
5.13.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Optional |
Explanatory |
N/A |
5.13.4 Description
FIPA will administer the name space of FIPA-services. This is part of the concrete realization process. Having a clear naming scheme for the FIPA-services will allow for optimised implementation and management of FIPA-services.
5.14 Locator
5.14.1 Summary
A locator consists of the set of transport-descriptions, which can be used to communicate with an FIPA-entity. An locator may be used by a message-transport-service to select a transport for communicating with the FIPA-entity, such as an agent or a FIPA-service. Locators can also contain references to software interfaces. This can be used when a FIPA-service can be accessed programmatically, rather than via a messaging model.
5.14.2 Relationships to Other Elements
Locator is a member of directory-entry,
which is registered with a directory-service
A locator contains one or
more transport-descriptions
A locator is used by message-transport-service to select a transport
5.14.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Single |
5.14.4 Description
The locator serves as a basic building block for managing address and transport resolution. An locator includes all of the transport-descriptions which may be used to contact the related agent or FIPA-service.
5.15 Message Encoding Representation
5.15.1 Summary
A message-encoding-representation is a way of representing an abstract syntax in a particular concrete syntax. Examples of possible representations are XML, FIPA strings, and serialized Java objects.
In principle, nested elements of the architecture may use different encodings – for example, a FIPA-message may be encoded in XML, and the resulting string used as the payload of a transport-message encoded as a CORBA object.
5.15.2 Relationships to Other Elements
Payload is encoded according to a message-encoding-representation.
FIPA-message is encoded according to a message-encoding-representation
Transport-message is encoded according
to a message-encoding-representation
Content is encoded according to a message-encoding-representation
5.15.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Functional |
5.15.4 Description
The way in which a message is encoded depends on the concrete architecture. If a particular architecture supports only one form of encoding, no additional information is required. If multiple forms of encoding are supported, messages may be made self-describing using techniques such as format tags, object introspection, and XML DTD references.
5.16 Message Transport Service
5.16.1 Summary
A message-transport-service is a FIPA-service. It supports the sending and receiving of transport-messages between agents.
5.16.2 Relationships to Other Elements
Message-transport-service may be invoked
to send a transport-message to an agent
Message-transport-service selects a transport based on the recipient's transport-description
Message-transport-service is a FIPA-service
5.16.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Optional |
Actual |
Functional |
5.16.4 Actions
A message-transport-service supports the following actions.
5.16.4.1 Bind Transport
An agent may contract with the message-transport-service to send and receive messages using a particular transport. It does this by invoking the bind-transport action of the message-transport-service. The semantics of this action are as follows:
The agent provides a transport-description corresponding to the transport which is to be used. (In initiating the action, the agent may control the scope of the action. Different reifications may handle this in different ways. The action may be addressed to a particular instance of a directory-service, or the action may be qualified with some kind of scope parameter.) Some or all of the elements of the transport-description may be missing, in which case the transport-service may supply appropriate values. The transport-service attempts to create a usable transport-end-point for the chosen transport-type, and constructs a transport-specific-address corresponding to this end-point.
If the action is successful, the message-transport-service will return an action-status indicating success, together with a transport-description which has been completely filled in and is usable for message transport. The agent may use this transport-description as part of its agent-description, and in constructing a transport-message.
Following a successful bind-transport, the message-transport-service will attempt to deliver any messages which are received over the transport end-point to the agent.
If the action is unsuccessful, the message-transport-service will return an action-status indicating failure, together with an explanation. The range of possible explanations is, in general, specific to a particular reification. However a conforming reification must, where appropriate, distinguish between the following explanations:
· Access – the agent making the request is not authorized to perform the specified action.
· Invalid – the transport-description is invalid in some way.
5.16.4.2 Unbind Transport
An agent may terminate a contract with the message-transport-service to send and receive messages using a particular transport. It does this by invoking the unbind-transport action of the message-transport-service. The semantics of this action are as follows:
The agent provides a transport-description which was returned by a previous bind-transport action. (In initiating the action, the agent may control the scope of the action. Different reifications may handle this in different ways. The action may be addressed to a particular instance of a directory-service, or the action may be qualified with some kind of scope parameter.) The transport-service identifies the corresponding transport-end-point and releases all transport-related resources.
If the action is successful, the message-transport-service will return an action-status indicating success. Additionally, the message-transport-service will no longer attempt to deliver any messages to the agent which are associated with the defunct transport binding.
If the action is unsuccessful, the message-transport-service will return an action-status indicating failure, together with an explanation. The range of possible explanations is, in general, specific to a particular reification. However a conforming reification must, where appropriate, distinguish between the following explanations:
· Not-found – the transport-description does not correspond to a bound transport.
· Access – the agent making the request is not authorized to perform the specified action.
· Invalid – the transport-description is invalid in some way.
5.16.4.3 Send Message
An agent may send a transport-message to another agent by invoking the send-message action of a message-transport-service. The semantics of this action are as follows:
The agent provides a transport-message which is to be sent. The message-transport-service examines the envelope of the message to determine how it should be handled.
If the action is successful, the message-transport-service will return an action-status indicating success. Following a successful send-message, the message-transport-service will make attempt to deliver the message to the recipient. However the successful completion of the send-message action should not be interpreted as indicating that delivery has been achieved.
If the action is unsuccessful, the message-transport-service will return an action-status indicating failure, together with an explanation. The range of possible explanations is, in general, specific to a particular reification. However a conforming reification must, where appropriate, distinguish between the following explanations:
· Access – the agent making the request is not authorized to perform the specified action.
· Invalid – the transport-message is invalid in some way.
5.16.4.4 Deliver Message
A message-transport-service may deliver a transport-message to an agent by invoking the deliver-message action of the agent. The semantics of this action are described under the heading for the bind-transport action.
5.16.5 Description
A concrete specification need not realize the notion of message-transport-service so long as the basic service provisions are satisfied. In the case of a concrete specification based on a single transport, the agent may use native operating system services or other mechanisms to achieve this service.
5.17 Ontology
5.17.1 Summary
An ontology is a set of symbols together with an associated interpretation that may be shared by a community of agents or software. An ontology includes a vocabulary of symbols referring to objects in the subject domain, as well as symbols referring to relationships that may be evident in the domain. An ontology also typically includes a set of logical statements expressing the constraints existing in the domain and restricting the interpretation of the vocabulary.
Ontologies provide a vocabulary for representing and communicating knowledge about some topic and a set of relationships and properties that hold for the entities denoted by that vocabulary.
5.17.2 Relationships to Other Elements
FIPA-message has an ontology
Content
has one or more
ontologies
5.17.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Functional |
5.17.4 Description
Ontologies must be nameable, findable and manageable. This is outlined in the future work section of this document.
5.18 Payload
5.18.1 Summary
A payload is an FIPA-message encoded in a manner suitable for inclusion in a transport-message.
5.18.2 Relationships to Other Elements
Payload is an encoded FIPA-message
Transport-message contains a payload
Payload is encoded according to a message-encoding-representation
5.18.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Single |
5.18.4 Description
???
5.19 Transport
5.19.1 Summary
A transport
is a particular data delivery service, such as a message transfer system, a
datagram service, a byte stream, or a shared whiteboard. Abstractly, a transport is a delivery system selected by virtue of the transport-description used to deliver
messages to an agent.
5.19.2 Relationships to Other Elements
Transport-description can be mapped onto a transport
Message-transport-service may use one or more transports to effect message delivery
A transport
may support one or more transport-encodings
5.19.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Functional |
5.19.4 Description
The mapping from transport-description to transport must be consistent across all realizations. FIPA will administer ontology of transport names. Concrete specifications should define a concrete encoding for this ontology.
5.20 Transport Description
5.20.1 Summary
A transport-description is a key-value tuple containing a transport-type, a transport-specific-address and zero or more transport-specific-properties.
5.20.2 Relationships to Other Elements
Transport-description has a transport-type
Transport-description has a set of transport-specific-properties.
Transport-description has a transport-specific-address.
Directory-entries includes one or more transport-descriptions.
Envelopes contain one or more
transport-descriptions
5.20.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Single |
5.20.4 Description
Transport-descriptions are used in three places within the abstract architecture. They are included in the directory-service, describing where a registered agent may be contacted. They can be included in the envelope for a transport-message, to describe how to deliver the message. In additions, if a message-transport-service is implemented, transport-descriptions are used as input to the message-transport-service to specify characteristics for additional delivery requirements for the delivery of messages to an agent.
5.21 Transport Message
5.21.1 Summary
A transport-message is the object conveyed from agent to agent. It contains the transport-description for the sender and receiver together with a payload containing the FIPA-message.
5.21.2 Relationships to Other Elements
Transport-message contains one or more transport-descriptions for the receiving agents
Transport-message contains a payload
Transport-message contains an envelope
Transport-message is encoded according to a message-encoding-representation
5.21.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Single |
5.21.4 Description
A concrete implementation may limit the number of receiving transport-descriptions for a transport-message. It may also establish particular relationships between the agent-name or agent-names for the receiver in the payload For example, it may ensure that there is a one-to-one correspondence between agent-names.
The important thing to convey from agent to agent is the payload, together with sufficient transport-message context to send a reply. A gateway or other transformation mechanism may unpack and reformat a transport-message as part of its processing.
5.22 Transport Specific Properties
5.22.1 Summary
A transport-specific-property is property associated with a transport-type. These properties are used by the transport-service to help it in constructing transport connections, based on the properties specified.
5.22.2 Relationships to Other Elements
Transport-description
includes zero or more transport-specific-properties.
5.22.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Single |
5.22.4 Description
The transport-specific-properties are not required for a particular transport. They may vary between transports.
5.23 Transport Type
5.23.1 Summary
A transport-type describes the type of transport which is associated with an transport-specific-address.
5.23.2 Relationships to Other Elements
Transport-description
includes a transport-type
5.23.3 Relationship to Concrete Specification
|
Mandatory/Optional |
Actual/Explanatory |
Single/Functional |
|
Mandatory |
Actual |
Single |
5.23.4 Description
FIPA will administer an ontology of transport-types. FIPA managed types will be flagged with the prefix of "FIPA-". Specific realizations can provide experimental types, which will be prefixed "X-"
6 Evolution of the Architecture
It is important that a document such as this be able to change to reflect new technologies and software engineering practices, and to correct errors, mistakes or poor choices. However extreme care must be taken when proposing any change, since an ill-considered change could, in principle, invalidate all concrete architectural specifications which are based upon this document.
For this reason it is recommended that new architectural elements be introduced only after they have been the subjects of substantial practical experience. When in doubt, new elements should be proposed as optional elements, and restricted to mutually consenting platform implementations. New properties and relationships for existing architectural elements must be introduced in a backward-compatible fashion; specifically, the change must support (and require) that all concrete implementations can incorporate the change in a backward compatible manner.
Much of our understanding about how to extend the FIPA architecture will depend on the use of experimental systems. It is useful to be able to deploy and test such systems without breaking “production” systems based on FIPA standard specifications. FIPA may elect to define specific ontologies or extend existing architectural elements in order to support experimental features in a well-behaved fashion. (A parallel may be drawn with the use of RFC-822 email systems, in which experimental elements may be introduced provided that they use names that begin “X-“.)
One of the challenges involved in creating the current set of abstractions is drawing the line between elements that belong in the abstract architecture and those which belong in concrete instantiations of the architecture. As FIPA creates several concrete specifications, and explores the mechanisms required to properly manage interoperation of these implementations, some features of the concrete architectures may be abstracted and incorporated in the FIPA abstract architecture. Likewise, certain abstract architectural elements may eventually be dropped from the abstract architecture, but may continue to exist in the form of concrete realizations.
The current placement of various elements as mandatory or optional, as well as actual or explanatory, is somewhat tentative. It is possible that some elements that are currently optional will, upon further experience in the development of the architecture become mandatory. Likewise, explanatory elements may be introduced in order to clarify the architecture, and may over time be reclassified as realized.
7 Informative Annex A: Goals of Message Transport Abstractions
7.1 Scope
In order to create abstractions for the various architectural elements, it is necessary to examine the kinds of systems and infrastructures that are likely targets of real implementations of the abstract architecture. In this section, we examine some of the ways in which concrete messaging and messaging transports may differ. Authors of concrete architectural specifications must take these issues into account when considering what end-to-end assumptions they can safely make. The goals describe below give the reader an understanding of the objectives the authors of the abstract architecture had in mind when creating this architecture.
7.2 Variety of Transports
There is a wide variety of transport services that may be used to convey a message from one agent to another. The abstract architecture is neutral with respect to this variety. For any instantiation of the architecture, one must specify the set of transports that are supported, how new transports are added, and how interoperability is to be achieved. It is permissible for a particular concrete architecture to require that implementations of that architecture must support particular transports.
Different transports use a variety of different address representations. Instantiations of the message transport architecture may support mechanisms for validating addresses, and for selecting appropriate transport services based upon the form of address used. It is extremely undesirable for an agent to be required to parse, decode, or otherwise rely upon the format of an address.
The following are examples of transport services that may be used to instantiate this abstract architecture:
· Enterprise message systems such as those from IBM and Tibco.
· A Java Messaging System (JMS) service provider, such as Fiorano.
· CORBA IIOP used as a simple byte stream.
· Remote method invocation, using Java RMI or a CORBA-based interface.
· SMTP email using MIME encoding.
· XML over HTTP.
· Wireless Access Protocol.
· Microsoft Named Pipes.
7.3 Support for Alternative Transports Within a Single System
Many application programming environments offer developers a variety of network protocols and higher-level constructs from which to implement inter-process communications, and it is becoming increasingly common for services to be made available over several different communications frameworks. It is expected that some instantiations of the FIPA architecture will allow the developer or deployer of agent systems to advertise the availability of their services over more than one message transport.
For this reason, the notion of transport address is here generalized to that of destination. A destination is an object containing one or more transport addresses. Each address is represented in a format that describes (explicitly or implicitly) the set of transports for which it is usable. (The precise mapping from address to transport is left to the concrete specification, although in practice the mapping is likely to be one-to-one.)
In its simplest form, a destination may be a single address that unambiguously defines the transport for which it can be used.
7.4 Desirability of Transport Agnosticism
The abstract architecture is consistent with concrete architectures which provide "transport agnostic" services. Such architectures will provide a programming model in which agents may be more or less aware of the details of transports, addressing, and many other communications-related mechanisms. For example, one agent may be able to address another in terms of some "social name", or in terms of service attributes advertised through the agent directory service without being aware of addressing format, transport mechanism, required level of privacy, audit logging, and so forth.
Transport agnosticism may apply to both senders and recipients of messages. A concrete architecture may provide mechanisms whereby an agent may delegate some or all of the tasks of assigning transport addresses, binding addresses to transport end-points, and registering addresses in white-pages or yellow-pages directories to the agent platform.
7.5 Desirability of Selective Specificity
While transport agnosticism simplifies the development of agents, there are times when explicit control of specific aspects of the message transport mechanism is required. A concrete architecture may provide programmatic access to various elements in the message transport subsystem.
7.6 Connection-Based, Connectionless and Store-and-Forward Transports
The abstract architecture is compatible with connection-based, connectionless, and store-and-forward transports. For connection-based transports, an instantiation may support the automatic reestablishment of broken connections. It is desirable than instantiations that implement several of these modes of operation should support transport-agnostic agents.
7.7 Conversation Policies and Interaction Protocols
The abstract architecture specifies a set of abstract objects which allows for the explicit representation of “a conversation”, i.e. a related set of messages between interlocutors which are logically related by some interaction pattern. It is desirable that this property be achieved by the minimum of overhead at the infrastructure or message level; in particular, it is important that interoperability not be compromised by this. For example, an implementation may deliver messages to conversation-specific queues based on an interpretation of the message envelope. To achieve interoperability with an agent that does not support explicit conversations (i.e. which does not allow individual messages to be automatically associated with a particular higher-level interaction pattern), it is necessary to specify the way in which the message envelope must be processed in order to preserve conversational semantics.
Note: in the practice, we were not able to fully meet this goal. It remains a topic of future work.
7.8 Point-to-Point and Multiparty Interactions
The abstract architecture supports both point-to-point and multiparty message transport. For point-to-point interactions, an agent sends a message to an address that identifies a single receiving agent. (An instantiation may support implicit addressing, in which the destination is derived from the name of the intended recipient agent without the explicit involvement of the sender.) For multiparty message transport, the address must identify a group of recipients. The most common model for such message transport is termed "publish and subscribe", in which the address is a “topic” to which recipients may subscribe. Other models (e.g. "address lists") are possible.
Not all transport mechanisms support multiparty communications, and concrete architectures are not required to provide multiparty messaging services. Concrete architectures which do provide such services may support proxy mechanisms, so that agents and agent systems that only use point-to-point communications may be included in multiparty interactions.
7.9 Durable Messaging
Some commercial messaging systems support the notion of durable messages, which are stored by the messaging infrastructure and may be delivered at some later point in time. It is desirable that an agent message transport architecture should take advantage of such services.
7.10 Quality of Service
The term quality of service refers to a collection of service attributes that control the way in which message transport is provided. These attributes fall into a number of categories:
· performance,
· security,
· delivery semantics,
· resource consumption,
· data integrity,
· logging and auditing, and,
· alternate delivery.
Some of these attributes apply to a single message; others may apply to conversations or to particular types of message transport. Architecturally it is important to be able to determine what elements of quality of service are supported, to express (or negotiate) the desired quality of service, to manage the service features which are controlled via the quality of service, to relate the specified quality of service to a service performance guarantee, and to relate quality of service to interoperability specifications.
7.11 Anonymity
The abstract transport architecture supports the notion of anonymous interaction. Multiparty message transport may support access by anonymous recipients. An agent may be able to associate a transient address with a conversation, such that the address is not publicly registered with any agent management system or directory service; this may extend to guarantees by the message transport service to withhold certain information about the principal associated with an address. If anonymous interaction is supported, an agent should be able to determine whether or not its interlocutor is anonymous.
7.12 Message Encoding
It is anticipated that FIPA will define multiple message encodings together with rules governing the translation of messages from one encoding to another. The message transport architecture allows for the development of instantiations that use one or more message encodings.
7.13 Interoperability and Gateways
The abstract agent transport architecture supports the development of instantiations that use transports, encodings, and infrastructure elements appropriate to the application domain. To ensure that heterogeneity does not preclude interoperability, the developers of a concrete architecture must consider the modes of interoperability that are feasible with other instantiations. Where direct end-to-end interoperability is impossible, impractical or undesirable, it is important that consideration be given to the specification of gateways that can provide full or limited interoperability. Such gateways may relay messages between incompatible transports, may translate messages from one encoding to another, and may provide quality-of-service features supported by one party but not another.
7.14 Reasoning about Agent Communications
The agent transport architecture supports the notion of agents communicating and reasoning about the message transport process itself. It does not, however, define the ontology or conversation patterns necessary to do this, nor are concrete architectures required to provide or accept information in a form convenient for such reasoning.
7.15 Testing, Debugging and Management
In general, issues of testing, debugging, and management are implementation-specific and will not be addressed in an abstract architecture. Individual instantiations may include specific interfaces, actions, and ontologies that relate to these issues, and may specify that these features are optional or normative for implementations of the instantiation.
8 Informative Annex B: Goals of Directory Service Abstractions
This section describes the requirements and architectural elements of the abstract Directory Service. The directory service is that part of the FIPA architecture which allows agents to register information about themselves in one or more repositories, for those same agents to modify and delete this information, and for agents to search the repositories for information of interest to them. The information that is stored is referred to an directory-entry, and the repository is an agent directory.
8.1 Scope
The purpose of the abstract architecture is to identify the key abstractions that will form the basis of all concrete architectures. As such, it is necessarily both limited and non-specific. In this section, we examine some of the ways in which concrete directory services may differ.
8.2 Variety of directory services
There are several directory services which may be used to store agent descriptions. The abstract architecture is neutral with respect to this variety. For any instantiation of the architecture, one must specify the set of directory services that are supported, how new directory services are added, and how interoperability is to be achieved. It is permissible for a particular concrete architecture to require that implementations of that architecture must support particular directory services.
Different directory services use a variety of different representations for schemas and contents. Instantiations of the agent directory architecture may support mechanisms for hiding these differences behind a common API and encoding, such as the Java JNDI model or hyper-directory schemes. It is extremely undesirable for an agent to be required to parse, decode, or otherwise rely upon different information encodings and schemas.
The following are examples of directory systems that may be used to instantiate the abstract directory service:
· LDAP,
· NIS or NIS+,
· COS Naming,
· Novell NDS,
· Microsoft Active Directory,
· The Jini lookup service, and,
· A name service federation layer, such as JNDI.
8.3 Desirability of Directory Agnosticism
The abstract architecture is consistent with concrete architectures which provide "directory agnostic" services. Such a model will support agents that are more or less completely unaware of the details of directory services. A concrete architecture may provide mechanisms whereby an agent may delegate some or all of the tasks of assigning transport addresses, binding addresses to transport end-points, and registering addresses in all available directories to the agent platform.
8.4 Desirability of Selective Specificity
While directory agnosticism simplifies the development of agents, there are times when explicit control of specific aspects of the directory mechanism is required. A concrete architecture may provide programmatic access to various elements in the directory subsystem.
8.5 Interoperability and Gateways
The abstract directory architecture supports the development of instantiations that use directory services appropriate to the application domain. To ensure that heterogeneity does not preclude interoperability, the developers of a concrete architecture must consider the modes of interoperability that are feasible with other instantiations. Where direct end-to-end interoperability is impossible, impractical or undesirable, it is important that consideration be given to the specification of gateways that can provide full or limited interoperability. Such gateways may extract agent descriptions from one directory service, transform the information if necessary, and publish it through another directory service.
8.6 Reasoning about Agent Directory
The abstract directory architecture supports the notion of agents communicating and reasoning about the directory service itself. It does not, however, define the ontology or conversation patterns necessary to do this, nor are concrete architectures required to provide or accept information in a form convenient for such reasoning.
8.7 Testing, Debugging and Management
In general, issues of testing, debugging, and management are implementation-specific and will not be addressed in an abstract architecture. Individual instantiations may include specific interfaces, actions, and ontologies that relate to these issues, and may specify that these features are optional or normative for implementations of the instantiation.
9 Informative Annex C: Goals for Abstract Agent Communication Language
9.1 Goals of This Abstract Communication Language
The prime motivation for the FIPA ACL is the enabling of communication between agents in a way that allows them to derive semantically useful information without requiring an a-priori agreement as to the language used in the communication.
Abstractly, this is achieved by means of a combination of three aspects:
1. A range of message types, which are based on Searle's speech act theory and which are grounded in a sound logical framework.
2. A series of notations in which logical propositions, actions and objects can be expressed.
3. The use of explicitly referenced ontologies that allow agents to interpret the identifiers in a communication relative to one or more shared interpretations of those identifiers.
9.2 Scope of This Discussion
The scope of this discussion is the concepts, structures and semantics required to support the three aspects identified above, taking into account the context of other elements of FIPA specifications, in particular the FIPA abstract architecture.
9.3 Requirements
9.3.1 Variety of content languages
There is considerable scope for variation in the particular content languages; some content languages may be highly specialized to particular domains and some may be extremely general and powerful. In the case where the content language is highly specialized, explicit ontologies may be less relevant since the ontology may be effectively frozen in to the content language. In the case where content languages are extremely general and powerful, the content language can express shared conditional plans or other propositions, in which case ontologies become quite important.
The FIPA AACL must therefore be able to represent a wide variety of content languages in a consistent manner.
9.3.2 Content Languages for FIPA
There is also scope for the use of content languages within FIPA itself; for example in the specification of agent management, or in the application scenarios, or in specific areas such as agent-human interactions. The demand for content languages in specifications produced by FIPA is likely to grow in the future.
Any content language(s) chosen by FIPA need to strike a balance between expressive power and simplicity. FIPA uses various subsets of predicate logic as a semantic base for FIPA's own content languages because that approach maximizes the links with the semantic framework of ACL itself.
9.3.3 Small Content Languages
Not every application domain requires the expressive power of full first order logic. There are many (if not most) situations where a much simpler language is sufficient. In the spirit of this, we do not require that all content languages (i.e., all concrete ACLs) be capable of representing all of the elements of the AACL.
The minimal requirements of a concrete content language are set by the kinds of messages (in particular the performatives that may be used in those message) that may be used in the application domain. For example, if an application domain does not require the denotation of actions, then the corresponding concrete content language does not need to have a method of representing actions - except for the specific actions denoted by the specific speech actions needed. Furthermore, it is not necessarily required that speech acts may be embedded within content language expressions. Therefore, it is required that any FIPA AACL be easily partitioned into semantically coherent subsets.
Any particular description of a content language should, moreover, show clearly which elements of the AACL are representable in the content language.
9.3.4 Variety of Language Expressions
On a large scale, software systems can often be viewed as being composed of islands of relatively tightly integrated components bridged together by specialized gateways. It is often the case that communication between the residents of an island can be richer than communication across islands - by virtue of the fact that there may be greater commonality and shared assumptions between components within a single island.
Independent of the particular content language in use, different platforms will tend to support very different program structures. For example, a Java-native community of agents may wish to communicate about Java objects in a natural way; and therefore, a Java-natural representation of a content expression would most naturally take the form of a parse tree-like structure consisting of Java objects. On the other hand, a LISP-native community of agents would prefer content language expressions as LISP S-expressions. This applies both internally to an agent and externally between agents.
Therefore, an important objective of the AACL is to enable relatively homogenous groups of agents to maximize the benefit of that homogeneity. This can be done by permitting the communication of values in a natural way while at the same time supporting a minimal range of data values that can be supported reasonably by all modern environments.
For example, in a community of Java agents, they should be able to incorporate Java objects directly in messages - this may be useful even if it is not possible or meaningful to send Java objects in messages to non-Java agents.
In addition to supporting native data values efficiently, the representation of messages themselves may be different in different environments. Again, a Java agent would be more efficient manipulating (and therefore understanding) an ACL message as a tree of Java objects representing the parse tree than as a string; whereas a PERL agent would tend to prefer a string representation given PERL's very powerful string handling features.
Therefore, an additional goal of the AACL is to allow multiple representations of content expressions; whilst at the same time constraining them to be semantically coherent across platforms.
9.3.5 Desirability of Logic
Logic - in particular predicate calculus - has been shown to be a very powerful formalism for expressing both mathematics and simpler concepts. The formalism itself is separate from the written notation, allowing many languages to have a semantic basis in logic. The prime benefit of a logical foundation is predictability: given a logical semantics it is possible to accurately predict the meaning of expressions (within the limitations of the interpretation of the particular symbols in the language which may be `outside' the logic).
9.3.5.1 Desirability of Logical Agnosticism
As noted above, the potential range of content languages is quite large; with a correspondingly large variety of semantic frameworks. However, the semantics of ACL itself is necessarily and firmly based in predicate calculus. Therefore it is required that there be some connection between the semantics of content languages and the semantics of ACL itself.
The full realization of this is strictly impossible since there are many systems of reasoning which cannot be formalized as logic. However, for many practical purposes, it is possible to express the semantics of most programming languages and most communications languages in logic. Furthermore, most applications involving the FIPA ACL are likely to be simple in nature and easily modelled in logic.
10 Informative Annex D: Goals for Security and Identity Abstractions
10.1 Introduction
In order to create abstractions for the various architectural elements, it is necessary to examine the kinds of systems and infrastructures that are likely targets of real implementations of the abstract architecture. In this section, we examine some of the ways in which security related issues may differ. Authors of concrete architectural specifications must take these issues into account when considering what end-to-end assumptions they can safely make. The goals describe below give the reader an understanding of the objectives the authors of the abstract architecture had in mind when creating this architecture.
In practice, only a very minor part of the security issues can be addressed in the abstract architecture, as most security issues are tightly coupled to their implementation.
In general, the amount of security required is highly dependent on the target deployment environment.
A glossary of security related terms is at the end of this section.
10.2 Overview
There are several aspects to security, which must permeate the FIPA architecture. They are:
· Identity. The ability to determine the identity of the various entities in the system. By identifying an entity, another entity interacting with it can determine what policies are relevant to interactions with that entity. Identity is based on credentials, which are verified by a Credential Authority.
· Access Permissions. Based on the identity of an entity, determine what policies apply to the entity. These policies might govern resource consumption, types of file access allowed, types of queries that can be performed, or other controlling policies.
· Content Validity. The ability to determine whether a piece of software, a message, or other data has been modified since being dispatched by its originating source. This is often accomplished by digitally signing data, and then having the recipient verify the contents are unchanged. Other mechanisms such as a hash algorithms can also be applied.
·
Content Privacy. The ability to ensure that only designated identities can examine
software, a message or other data. To all others the information is obscured.
This is often accomplished by encrypting the data, but can also be accomplished
by transporting the data over channels that are encrypted.
· Identity, or the use of credentials, is needed to supply the ability to control access, to provide content validity, and create content privacy. Each of these is discussed below.
10.3 Areas to Apply Security
This section describes the areas in which security can be applied within agent systems. In each case, the security related risks that are being guarded against are described. The assumption is that any agent or other entity in the system may have credentials which can be used to perform various validation.
10.3.1 Content Validity and Privacy During Message Transport
There are two basic potential security risks when sending a message from one agent to another.
The first risk is that a message is intercepted, and modified in some way. For example, the interceptor software inserts several extra numbers into a payment amount, and modifies the name of the check payee. After modification, it is sent on to the original recipient. The other agent acts on the incorrect data. In a case like this, the content validity of the message is broken.
The second risk is that the message is read by another entity, and the data in it is used by that entity. The message does reach its original destination intact. If this occurs, the privacy of the message is violated.
Digital signing and encryption can address these risks, respectively. These two techniques can be abstractly presented at two different layers of the architecture. The messages themselves (or probably just the payload part) can be signed or encrypted. There are a number of techniques for this, PGP signing and encryption, Public Key signing and encryption, one time transmission keys, and other cryptographic techniques. This approach is most effective with the nature of underlying message transport is unknown or unreliable from a security perspective.
The message transport itself can also provide the digital signing or encryption. There are a number of transports that can provide such features: SKIP, IPSEC, CORBA Common Secure Interoperability Services. It seems prudent to include both models within the architecture, since different applications and software environments will have very different capabilities.
There is another aspect of message transport privacy that comes from agents which misrepresent themselves. In this scenario, an agent can register with directory services indicating that is a provider of some service, but in fact uses the data it receives for some other purpose. To put it differently, how do you know who you are talking to? This topic is covered under agent identity.
10.3.2 Agent Identity
If agents and agent services have a digital identity, then agents can validate that:
· Agents they are exchanging messages with can be accurately identified, and,
· Services they are using are from a known, safe source
Similarly, services can determine whether the agent:
· Use identity to determine code access or access control decisions, or,
· Use agent identity for non-repudiation of transactions.
10.3.3 Agent Principal Validation
The Agent can contain a principal (for example a user), on whose behalf this code is running. The principal has one or more credentials, and the credentials may have one or more roles that represent the principal.
If an agent has a
principal, the other agents can:
· Determine whether they want to interoperate with that agent,
· Determine what policy and access control to permit to that user, and,
· Use the identity to perform transactions.
Services could perform similar actions.
10.3.4 Code signing validation
An agent can be code signed. This involves digitally signing the code with one or more credentials. If an agent is code signed, the platform could:
· Validate the credential(s) used to sign the agent software. Credentials are validated with a credential authority,
· If the credentials are valid, use policy to determine what access this code will have, or,
· If the credentials are valid, verify that the code is not modified.
In addition, the Agent Platform can use the lack of digital signature
to determine whether to allow the code to run, and policy to determine what
access the code will have. In other words, some platforms may have the policy
that will not permit code to run, or will restrict Access Permissions unless it
is digitally signed.
10.4 Risks Not Addressed
There are a number of other possible security risks that are not addressed, because they are general software issues, rather than unique or special to agents. However, designers of agent systems should keep these issues in mind when designing their agent systems.
10.4.1 Code or Data Peeping
An entity can probe the running agent and extract useful information.
10.4.2 Code or Data Alteration
The unauthorized modification or corruption of an agent, its state, or data. This is somewhat addressed by the code signing, which does not cover all cases.
10.4.3 Concerted Attacks
When a group of agents conspire to reach a set of goals that are not desired by other entities. These are particularly hard to guard against, because several agents may co-operate to create a denial of service attack which is a feint to allow another agent to undertake the undesirable action.
10.4.4 Copy and Replay
An attempt to copy an agent or a message and clone or retransmit it. For example, a malicious platform creates an illegal copy, or a clone, of an agent, or a message from an agent is illegally copied and retransmitted.
10.4.5 Denial of Service
In a denial-of-service the attackers try to deny resources to the platform or an agent. For example, an agent floods another agent with requests and the receiving agent is unable to provide its services to other agents.
10.4.6 Misinformation Campaigns
The agent, platform, or service misrepresents information. This includes lying during negotiation, deliberately representing another agent, service or platform as being untrustworthy, costly, or undesirable.
10.4.7 Repudiation
An agent or agent platform denies that it has received/sent a message or taken a specific action. For example, a commitment between two agents as the result of a contract negotiation is later ignored by one of the agents, denying the negotiation has ever taken place and refusing to honour its part of the commitment.
10.4.8 Spoofing and Masquerading
An unauthorized agent or service claims the identity of another agent or piece of software. For example, an agent registers as a Directory Service and therefore receives information from other registering agents.
10.5 Glossary of Security Terms
Access permission – Based on a credential model, the ability to allow or disallow software from taking an action. For example, software with certain credentials may be allowed read a particular file, a group with different credentials may be allowed to write to the file.
Examples: OS file system permissions, Java Security Profiles (check name), Database access controls.
Authentication – Using some credential model, ability to verify that the entity offering the credentials is who/what it says it is.
Credential – An item offered to prove that a user, a group, a software entity, a company, or other entities is who or what it claims to be.
Examples: X.509 certificate, a user login and password pair, a PGP key, a response/challenge key, a fingerprint, a retinal scan, a photo id. (Obviously, some of these are better suited to software than others!)
Credential Authority – An entity that determines whether the credential offered is valid, and that the credential accurately identifies the individual offering it.
Examples: X.509 certificate can be validated by a certificate authority. At a bar, the bartender is the credential authority who determines whether your photo id represents you.(He then may determine your access permissions to the available beverages!).
Credential model – The particular mechanism(s) being used to provide and authenticate credentials.
Code signing – A particular case of digital signature (see below), where code is signed by the credentials of some entity. The purpose of code signing is to identify the source of the code, and to verify that the code has not been changed by another entity.
Examples: Java code signing, DCOM object signing, checksum verification.
Digital signature – Using a credential model to indicate the source of some data, and to ensure that the data is unchanged since it was signed. Note: the word data is used very broadly here – it could a string, software, voice stream, etc.
Examples: S/MIME mail, PGP digital signing, IPSEC (authentication modes)
Encryption – Ability to transform data into a format that can only be restored by the holder of a particular credential. Used to prevent data from being observed by others.
Examples: SSL, S/MIME mail, PGP digital signing, IPSEC (encryption modes)
Identity – A person, server, group, company, software program that can be uniquely identified. Identities can have credentials that identify them.
Lease – An interval of time that some element, such as an identity or a credential is good for. Leases are very useful when you want to restrict the length of commitment. For example, you may issue a temporary credential to an agent that gives it 20 minutes in a given system, at which time the credential expires.
Policy – Some set of actions that should be performed when a set of conditions is met. In the context of security, allow access permissions based on a valid credential that establishes an identity. <Need to merge this with policy concepts once we have them>
Examples: If a credential for a particular user is presented, allow him to access a file. If a credential for a particular role is presented, allow the agent to run with a low priority.
Role – An identity that has an “group” quality. That is, the role does not uniquely identify an individual, or machine, or an agent, but instead identifies the identity in a particular context: as a system manager, as a member of the entry order group, as a high-performance calculation server, etc.
Examples: In various operating system groups, as applied to file system access. In Lotus Notes, the “role” concept. X.509 certificate role attributes.
Principal – In the agent domain, the identity on whose behalf the agent is running. This may be a user, a group, a role, another software entity.
Examples: A shopping agent’s principal is the user who launched it. An commodity trader agent’s principal is a financial company. A network management agent’s principal is the role of system admin, or super-user. In a small “worker bee” agent, the principal may be the delegated authority of the parent agent
11 References
[FIPA00008] FIPA Content Language Library Specification. Foundation for Intelligent Physical Agents, 2000. http://www.fipa.org/specs/fipa00008/
[FIPA00023] FIPA Agent Management Specification. Foundation for Intelligent Physical Agents, 2000. http://www.fipa.org/specs/fipa00023/